Is Cloud-Based EHR Software HIPAA Compliant?
How well do you know the cloud? In a recent survey conducted, 29% of the participants believed the cloud has something to do with the weather, and 51% believed that the weather can affect cloud computing. It’s no wonder people easily dismiss the fact that cloud-based EHR software is HIPAA compliant and can be used for Meaningful Use.
We’re here to give you the facts about cloud-based EHR systems and how to complete a security risk analysis to be compliant with the Meaningful Use program.
Keeping Your EHR Software Secure
First things first - any system, including a cloud-based system, that has been certified for 2014 standards is HIPAA compliant and eligible to attest for Meaningful Use. Since HIPAA places strict privacy standards on all providers in the medical industry, all vendors, including cloud vendors, are required to give you the best security possible. In fact, EHR cloud vendors can provide better data security than most eyecare practices can accomplish in their own office. Reputable cloud vendors encrypt your data, use separate databases for each user, and host their systems in facilities that have security controls that many practices cannot afford to provide on their own.
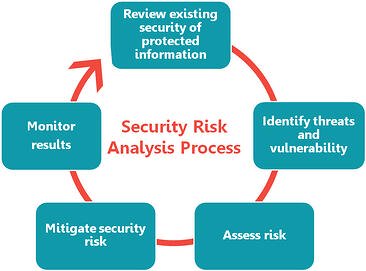 To make sure that your data is safe, part of the core objectives for Stage 1 and 2 of the Meaningful Use Program requires you to perform a full security risk analysis of your certified EHR. This way, both you and your vendor are responsible for the security and privacy of your data. Let’s go through the objective:
To make sure that your data is safe, part of the core objectives for Stage 1 and 2 of the Meaningful Use Program requires you to perform a full security risk analysis of your certified EHR. This way, both you and your vendor are responsible for the security and privacy of your data. Let’s go through the objective:
- Stage 1: Eligible professionals must conduct or review a security risk analysis and implement security updates as necessary and correct identified security deficiencies.
- Stage 2: Eligible professionals need to meet the same security risk analysis requirements as Stage 1, but must also address the encryption/security of data at rest.
Note: A security risk analysis needs to be conducted or reviewed during each reporting period for Stage 1 and Stage 2.
Once you have completed the risk analysis, you must take any additional steps to reduce identified risks. Even with a certified EHR, you must perform a full security risk analysis. Security requirements address all electronic protected health information you have in your practice, including equipment and third party software, not just what is in your EHR. Your EHR vendor may be able to provide help and training on the privacy and security aspects of the EHR product and show you how to meet the objective through the EHR.
See the following CMS resources for more information about the Risk Analysis requirement:
- Guide to Privacy and Security of Health Information
- Security Risk Analysis Tipsheet: Protecting Patients’ Health Information
Check out the following posts to find out more about cloud-based EHR software:
- Quiz: How Well Do You Know Cloud-Based EHR Software?
- How a Cloud-Based Practice Management and EHR Optimizes Your Practice
Looking for a cloud-based practice management and EHR software that's HIPAA compliant? Do you know what other things you should be looking for when shopping for software? Download our latest eBook to make sure you get all the answers you need to make a decision.

